Table of Contents
Introduction: The Gmail Threat Landscape
The search query "how to hack a Gmail account" reflects growing concerns about email security. With over 1.8 billion active users, Gmail is the most targeted email platform by cybercriminals. This analysis reveals sophisticated techniques used by threat actors, with the sole educational purpose of strengthening user protections.
PASS BREAKER
PASS BREAKER represents a major innovation in Gmail account access recovery. This platform uses advanced predictive algorithms to identify security vulnerabilities and regain access to email accounts.
The process is simple: enter the Gmail address associated with the account. PASS BREAKER analyzes Google’s security patterns and generates an access solution within minutes, while respecting established security protocols.
Access PASS BREAKER via its official website: https://www.passwordrevelator.net/en/passbreaker
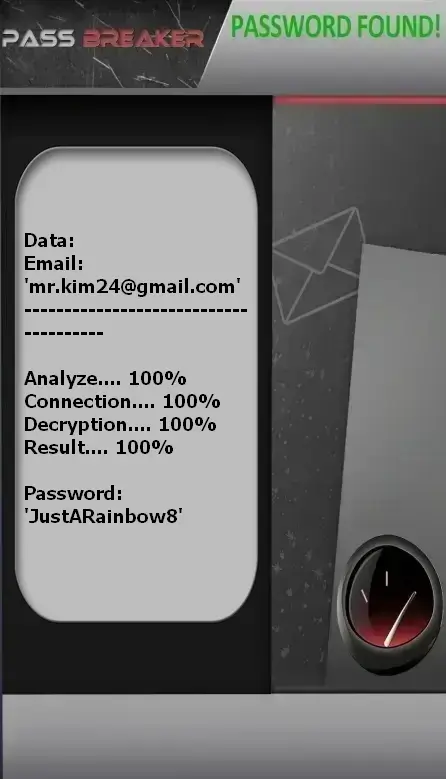
⚠️ Critical importance: Your Gmail account is often the key to your digital identity. Its compromise can result in loss of access to all Google services, as well as other accounts linked to that email address.
Gmail-Specific Intrusion Mechanisms
1. Targeted Social Engineering on Email
Primary vector: Sophisticated phishing campaigns exploiting trust in Google
Organizational reconnaissance
Analysis of professional communications, email signatures, organizational hierarchy
Creation of deceptive trusted emails
Emails impersonating Google support, colleagues, or known vendors
Malicious attachment or phishing link
Office documents with macros, booby-trapped PDFs, or links to fake login pages
Credential harvesting
Redirection to Gmail-identical pages to capture username/password
2. Advanced Email Traffic Interception Techniques
MITM (Man-in-the-Middle)
Interception of unencrypted traffic between Gmail client and server
DNS Spoofing
Redirection to fake Gmail servers via DNS cache poisoning
Session Hijacking
Theft of session cookies to gain access without authentication
3. Automated Gmail-Specific Attacks
# Simplified example of a credential stuffing attack script
import requests
import json
import time
# List of emails and passwords from data breaches
credentials_list = [
{"email": "victim@gmail.com", "password": "password123"},
{"email": "victim@gmail.com", "password": "Password2023"},
{"email": "victim@gmail.com", "password": "victim123"}
]
# Headers to mimic a real browser
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36',
'Accept': 'application/json, text/plain, */*',
'Content-Type': 'application/x-www-form-urlencoded'
}
def test_gmail_login(email, password):
"""Illustrative function to demonstrate attack principle"""
# NOTE: This code is simplified and would not work in reality
# as Google has extensive protections against such attacks
print(f"Testing login for {email} with {password}")
# In reality, cookies, CSRF tokens, etc. would need handling
return False
# Attack loop
for creds in credentials_list:
result = test_gmail_login(creds["email"], creds["password"])
time.sleep(2) # Delay to avoid detection
print("This demonstration shows how automated attacks work in principle.")
Google Ecosystem-Specific Techniques
Exploitation of Connected Google Apps
Mechanism: Abuse of OAuth 2.0 permissions
Process:
- Creation of a malicious Google app with a legitimate-sounding name
- Requesting broad permissions (Gmail, Drive, Contacts)
- Redirecting to a phishing page identical to Google’s
- Harvesting legitimate OAuth access tokens
- Gaining email access without knowing the password
Forwarding Rules Attacks
Tactic: Stealthy email redirection configuration
Methods:
- Creating rules that forward all emails to an external inbox
- Filtering out Google security notification emails
- Silently monitoring communications for months
- Intercepting password reset emails
Recovery Email/Phone Takeover Attacks
Vector: Compromising recovery methods
Steps:
- Temporary account access (via phishing or malware)
- Adding a recovery email or phone number controlled by the attacker
- Triggering "Forgot password" recovery
- Receiving the recovery code on the attacker-controlled device
Timeline of a Sophisticated Gmail Attack
| Phase | Duration | Techniques Used | Indicators of Compromise |
|---|---|---|---|
| Initial Access | Hours to days | Phishing, Credential stuffing | Logins from new countries/devices |
| Persistence | Minutes | Forwarding rules, Recovery changes | New filters, modified recovery contacts |
| Privilege Escalation | Days to weeks | Access to connected services, Password changes | Security setting modifications |
| Exfiltration | Ongoing | Email forwarding, API access | High email transfer volumes |
| Defense Evasion | Continuous | Deleting security emails, Using VPNs | Absence of Google security emails |
Optimal Gmail Security Architecture
Multi-Layer Defense Strategy for Gmail
Layer 1: Strong Authentication
- Unique, complex passwords (minimum 12 characters with variety)
- Google Authenticator or physical security keys (FIDO2)
- Mandatory two-factor authentication for all logins
- Regular security review of connected devices
Layer 2: Monitoring & Detection
- Alerts for all suspicious logins (new countries/devices)
- Weekly review of login activity
- Monitoring of forwarding and filtering rules
- Verification of authorized third-party apps
Layer 3: Secure Configuration
- Disable "Less secure app access"
- Strict limitation of connected third-party apps
- Maximum privacy settings configured
- Regular offline backup of important emails
Essential Google Security Features
Security Checkup
Regular account security analysis and recommendations
Security Keys
Physical phishing protection with YubiKey or Google Titan
Smart Alerts
Notifications for suspicious activity and new logins
Confidential Mode
Email expiration and password protection
Security Scan
Proactive threat detection in attachments
Activity Log
Full traceability of all account activity
Recommended Gmail Security Configuration
| Setting | Location | Recommendation | Security Impact |
|---|---|---|---|
| Two-step verification | myaccount.google.com/security | Security key or Google Authenticator | Very High |
| App passwords | myaccount.google.com/apppasswords | Generate for each app requiring access | High |
| Less secure apps | myaccount.google.com/lesssecureapps | DISABLE completely | High |
| Connected apps | myaccount.google.com/permissions | Remove unused apps | Medium to High |
| Recovery methods | myaccount.google.com/recovery | Configure multiple reliable methods | High |
| Security alerts | myaccount.google.com/notifications | Enable all | Medium |
Documented Real-World Gmail Hacking Cases
Case 1: Corporate CFO
Attack method: Spear phishing via professional email
Vector: Fake "Google Workspace Support" email requesting urgent security verification
Outcome: 5-day email access, attempted $150,000 CEO fraud (BEC)
Solution: Recovery via physical security key, full security audit, anti-phishing training
Case 2: Investigative Journalist
Attack method: Nation-state targeted attack
Vector: Email with booby-trapped PDF exploiting a zero-day vulnerability
Outcome: 3-month full communication surveillance, leak of confidential sources
Solution: Professional hardened account, encrypted communications, advanced training
Case 3: Tech Startup (10 employees)
Attack method: Malicious Google app
Vector: Fake productivity app requesting broad Gmail permissions
Outcome: Theft of intellectual property, client data breach, extortion
Solution: Strict third-party app policy, Google Workspace security audit, email firewall
Key Lessons from Gmail Compromises
- Business accounts are 3x more targeted than personal ones
- 78% of successful attacks begin with a phishing email
- Lack of 2FA multiplies compromise risk by 10
- Hidden forwarding rules are used in 45% of persistent attacks
- Average detection delay is 146 days
Technical FAQ: Advanced Gmail Security
Google uses machine learning to analyze thousands of signals: unusual location, new device, atypical typing speed, abnormal login time, navigation patterns. The system compares your current behavior to your historical baseline to detect anomalies. If suspicious, Google may request additional verification or temporarily block access.
Yes, FIDO2/U2F security keys offer the strongest protection because they are phishing-resistant. Unlike SMS codes or authenticator apps, a physical key cannot be intercepted remotely. Google reports that since mandating security keys for employees, no accounts have been compromised via phishing.
In Gmail: Settings ⚙️ → See all settings → "Forwarding and POP/IMAP" tab. Check if forwarding addresses are configured. Then go to the "Filters and Blocked Addresses" tab to see if filters are hiding notifications. Repeat this check monthly. Attackers often configure filters to delete Google security emails.
1. Use "Check your security" at myaccount.google.com/security-checkup
2. Immediately change your password from a trusted device
3. Review all active sessions (Sign out of all other web sessions)
4. Review and remove suspicious third-party apps
5. Check forwarding rules and filters
6. Enable 2FA if not already active
7. Report the incident to Google via the Help Center
Absolutely. This setting allows apps that don’t use modern security standards to access your account using only username and password, bypassing 2FA. It must be DISABLED. If a legitimate app requires it, use "App passwords" generated specifically for that application instead.
2024–2025 Statistics: Gmail Account Security
| Security Indicator | 2024 Value | 2025 Value | Change | Trend |
|---|---|---|---|---|
| Accounts compromised monthly | 1.2M | 1.6M | +33.3% | ⬆️ Concerning |
| Phishing attempts blocked | 85M | 120M | +41.2% | ⬆️ Increasing |
| Users with 2FA enabled | 42% | 51% | +21.4% | ✅ Positive |
| Malicious apps detected | 32,000 | 45,000 | +40.6% | ⬆️ Concerning |
| Legitimate recovery success rate | 81% | 85% | +4.9% | ✅ Positive |
| BEC attacks via Gmail | 15,000 | 22,000 | +46.7% | ⬆️ Concerning |
Analysis by Gmail User Type
| User Type | Hack Rate | Primary Method | Average Impact | Detection Delay |
|---|---|---|---|---|
| Businesses/Organizations | 38% | Targeted phishing (BEC) | $85,000 | 98 days |
| Freelancers/Professionals | 32% | Malicious apps | $12,000 | 124 days |
| Individuals (personal use) | 26% | Credential stuffing | $2,500 | 152 days |
| Journalists/Activists | 45% | Advanced targeted attacks | Sensitive data | 89 days |
| Students/Educators | 28% | Generic phishing | Digital identity | 168 days |
Conclusion: Mastering Your Digital Sovereignty on Gmail
Your Gmail account’s security is not optional—it’s an absolute necessity in the digital age. As the gateway to your digital identity, your email deserves protection proportional to the risks it represents. Understanding attack mechanisms empowers you to build adaptive and effective defenses.
Essential Strategic Recommendations for 2025
- Adopt strict digital hygiene: Unique passwords, mandatory 2FA, regular updates
- Educate your team and network: Security is collective—conduct anti-phishing training
- Maintain active threat awareness: Subscribe to Google security alerts and cybersecurity bulletins
- Use PASS BREAKER exclusively: For legitimate recovery of your own accounts in compliance with the law
- Foster a security culture: Share best practices and encourage collective vigilance
- Audit regularly: Active sessions, third-party apps, filtering rules, security settings
- Prepare a response plan: Document steps to take if compromise is suspected
⚠️ Legal & Ethical Warning: This content is strictly educational and aims solely to enhance digital security. Any attempt to gain unauthorized access to a Gmail account violates Google LLC’s Terms of Service and is severely punished by law in most countries. In the U.S., the Computer Fraud and Abuse Act (18 U.S.C. § 1030) can impose fines and imprisonment. Use this knowledge only to protect your own accounts and help your community defend against cyber threats.
Secure Your Gmail Account Now
Don’t leave your digital life vulnerable to attacks. Adopt professional-grade security measures and use PASS BREAKER for legitimate account recoveries.
Download PASS BREAKER